19.2: Computer Security
- Page ID
- 72866
\( \newcommand{\vecs}[1]{\overset { \scriptstyle \rightharpoonup} {\mathbf{#1}} } \)
\( \newcommand{\vecd}[1]{\overset{-\!-\!\rightharpoonup}{\vphantom{a}\smash {#1}}} \)
\( \newcommand{\dsum}{\displaystyle\sum\limits} \)
\( \newcommand{\dint}{\displaystyle\int\limits} \)
\( \newcommand{\dlim}{\displaystyle\lim\limits} \)
\( \newcommand{\id}{\mathrm{id}}\) \( \newcommand{\Span}{\mathrm{span}}\)
( \newcommand{\kernel}{\mathrm{null}\,}\) \( \newcommand{\range}{\mathrm{range}\,}\)
\( \newcommand{\RealPart}{\mathrm{Re}}\) \( \newcommand{\ImaginaryPart}{\mathrm{Im}}\)
\( \newcommand{\Argument}{\mathrm{Arg}}\) \( \newcommand{\norm}[1]{\| #1 \|}\)
\( \newcommand{\inner}[2]{\langle #1, #2 \rangle}\)
\( \newcommand{\Span}{\mathrm{span}}\)
\( \newcommand{\id}{\mathrm{id}}\)
\( \newcommand{\Span}{\mathrm{span}}\)
\( \newcommand{\kernel}{\mathrm{null}\,}\)
\( \newcommand{\range}{\mathrm{range}\,}\)
\( \newcommand{\RealPart}{\mathrm{Re}}\)
\( \newcommand{\ImaginaryPart}{\mathrm{Im}}\)
\( \newcommand{\Argument}{\mathrm{Arg}}\)
\( \newcommand{\norm}[1]{\| #1 \|}\)
\( \newcommand{\inner}[2]{\langle #1, #2 \rangle}\)
\( \newcommand{\Span}{\mathrm{span}}\) \( \newcommand{\AA}{\unicode[.8,0]{x212B}}\)
\( \newcommand{\vectorA}[1]{\vec{#1}} % arrow\)
\( \newcommand{\vectorAt}[1]{\vec{\text{#1}}} % arrow\)
\( \newcommand{\vectorB}[1]{\overset { \scriptstyle \rightharpoonup} {\mathbf{#1}} } \)
\( \newcommand{\vectorC}[1]{\textbf{#1}} \)
\( \newcommand{\vectorD}[1]{\overrightarrow{#1}} \)
\( \newcommand{\vectorDt}[1]{\overrightarrow{\text{#1}}} \)
\( \newcommand{\vectE}[1]{\overset{-\!-\!\rightharpoonup}{\vphantom{a}\smash{\mathbf {#1}}}} \)
\( \newcommand{\vecs}[1]{\overset { \scriptstyle \rightharpoonup} {\mathbf{#1}} } \)
\(\newcommand{\longvect}{\overrightarrow}\)
\( \newcommand{\vecd}[1]{\overset{-\!-\!\rightharpoonup}{\vphantom{a}\smash {#1}}} \)
\(\newcommand{\avec}{\mathbf a}\) \(\newcommand{\bvec}{\mathbf b}\) \(\newcommand{\cvec}{\mathbf c}\) \(\newcommand{\dvec}{\mathbf d}\) \(\newcommand{\dtil}{\widetilde{\mathbf d}}\) \(\newcommand{\evec}{\mathbf e}\) \(\newcommand{\fvec}{\mathbf f}\) \(\newcommand{\nvec}{\mathbf n}\) \(\newcommand{\pvec}{\mathbf p}\) \(\newcommand{\qvec}{\mathbf q}\) \(\newcommand{\svec}{\mathbf s}\) \(\newcommand{\tvec}{\mathbf t}\) \(\newcommand{\uvec}{\mathbf u}\) \(\newcommand{\vvec}{\mathbf v}\) \(\newcommand{\wvec}{\mathbf w}\) \(\newcommand{\xvec}{\mathbf x}\) \(\newcommand{\yvec}{\mathbf y}\) \(\newcommand{\zvec}{\mathbf z}\) \(\newcommand{\rvec}{\mathbf r}\) \(\newcommand{\mvec}{\mathbf m}\) \(\newcommand{\zerovec}{\mathbf 0}\) \(\newcommand{\onevec}{\mathbf 1}\) \(\newcommand{\real}{\mathbb R}\) \(\newcommand{\twovec}[2]{\left[\begin{array}{r}#1 \\ #2 \end{array}\right]}\) \(\newcommand{\ctwovec}[2]{\left[\begin{array}{c}#1 \\ #2 \end{array}\right]}\) \(\newcommand{\threevec}[3]{\left[\begin{array}{r}#1 \\ #2 \\ #3 \end{array}\right]}\) \(\newcommand{\cthreevec}[3]{\left[\begin{array}{c}#1 \\ #2 \\ #3 \end{array}\right]}\) \(\newcommand{\fourvec}[4]{\left[\begin{array}{r}#1 \\ #2 \\ #3 \\ #4 \end{array}\right]}\) \(\newcommand{\cfourvec}[4]{\left[\begin{array}{c}#1 \\ #2 \\ #3 \\ #4 \end{array}\right]}\) \(\newcommand{\fivevec}[5]{\left[\begin{array}{r}#1 \\ #2 \\ #3 \\ #4 \\ #5 \\ \end{array}\right]}\) \(\newcommand{\cfivevec}[5]{\left[\begin{array}{c}#1 \\ #2 \\ #3 \\ #4 \\ #5 \\ \end{array}\right]}\) \(\newcommand{\mattwo}[4]{\left[\begin{array}{rr}#1 \amp #2 \\ #3 \amp #4 \\ \end{array}\right]}\) \(\newcommand{\laspan}[1]{\text{Span}\{#1\}}\) \(\newcommand{\bcal}{\cal B}\) \(\newcommand{\ccal}{\cal C}\) \(\newcommand{\scal}{\cal S}\) \(\newcommand{\wcal}{\cal W}\) \(\newcommand{\ecal}{\cal E}\) \(\newcommand{\coords}[2]{\left\{#1\right\}_{#2}}\) \(\newcommand{\gray}[1]{\color{gray}{#1}}\) \(\newcommand{\lgray}[1]{\color{lightgray}{#1}}\) \(\newcommand{\rank}{\operatorname{rank}}\) \(\newcommand{\row}{\text{Row}}\) \(\newcommand{\col}{\text{Col}}\) \(\renewcommand{\row}{\text{Row}}\) \(\newcommand{\nul}{\text{Nul}}\) \(\newcommand{\var}{\text{Var}}\) \(\newcommand{\corr}{\text{corr}}\) \(\newcommand{\len}[1]{\left|#1\right|}\) \(\newcommand{\bbar}{\overline{\bvec}}\) \(\newcommand{\bhat}{\widehat{\bvec}}\) \(\newcommand{\bperp}{\bvec^\perp}\) \(\newcommand{\xhat}{\widehat{\xvec}}\) \(\newcommand{\vhat}{\widehat{\vvec}}\) \(\newcommand{\uhat}{\widehat{\uvec}}\) \(\newcommand{\what}{\widehat{\wvec}}\) \(\newcommand{\Sighat}{\widehat{\Sigma}}\) \(\newcommand{\lt}{<}\) \(\newcommand{\gt}{>}\) \(\newcommand{\amp}{&}\) \(\definecolor{fillinmathshade}{gray}{0.9}\)Computer security is a branch of information technology known as information security which is intended to protect computers. Computer security has three main goals:
- Confidentiality: Making sure people cannot acquire information they should not (keeping secrets)
- Integrity: Making sure people cannot change information they should not (protecting data)
- Availability: Making sure people cannot stop the computer from doing its job.
Computer security involves telling computers what they are not to do. This makes computer security unique because most programming makes computers do things. Security takes much of a computers power.
Basic computer security methods (in approximate order of strength) can be:
- Limit access to computers to “safe” users.
- Peripherals which block any “unsafe” activity.
- Firewall and antivirus software.
An example of complexity and pervasiveness of the issue is vending machines, per Hackers Lurking in Vents and Soda Machines April 7, 2014 New York Times.
Malware
Malware, short for malicious software, is a kind of software that can be installed on a computer without approval from the computer’s owner. There are different kinds of malware that can hurt computers, such as viruses and spyware. These programs can steal passwords, delete files, collect personal information, or even stop a computer from working at all. Computer security or anti-malware software is usually good at stopping malware from installing itself. When security software isn’t installed, malware can get into the computer. Getting rid of malware can be difficult, even when using programs designed to remove it.
History
People first started writing malware in the 1970s and early 1980s. Computers were very simple then. They did not have any interesting information for malware to take. Instead, people wrote malware for fun[1] or just to show that they could.[2] Even the most common piece of malware from this time did not do damage to people’s computers.[3] In fact, malware was so rare that the word “malware” was not coined until 1990.[4]
More people started using the computers in the late 1990s and early 2000s. Computers were getting more complex just as fast.[5] People saw that they could use malware to get useful information now, like passwords and credit card information. So, more programmers started writing malware. The number of malware programs on the Internet has grown very quickly ever since then the late 1990s and is still growing today.[6] Experts think that 31.5% of the world’s computers have some type of malware installed.[7]
Purposes
The main reason people write malware is to hurt others and make money, usually by stealing or deleting important information. The Cryptolocker computer virus, for example, makes it so a person cannot use their own computer until they pay the malware writers for a software key to unlock it.[8] Another virus, CIH, tries to make it so the victim can never use their files or turn on their computer again.[9] Malicious keystroke logging software remembers everything a user types in and gives it to the malware author to read.[10]
World governments have written malware to hurt their enemies. Experts think that the United States government made a virus named Stuxnet to stop an important place in Iran from working.[11] The Chinese government probably used a virus to stop people from protesting its decisions.[12]
How Malware Gets Installed
There are a lot of ways malware can get onto someone’s computer. One common way is through email attachments. These attachments are usually sent from other computers that already have malware on them.[13] When someone downloads and opens the attachment, the virus installs and uses their computer to send itself to even more people.
Another way malware installs itself is when a victim gets malware just by going to a website with the malware hidden on it. This is called drive-by downloading. A user does not have to click anything for their computer to get infected from a drive-by download.[14] This kind of malware attack is usually found on websites that are not used a lot or whose security methods are very old. However, even current websites that people use all the time can host drive-by downloads when someone hacks the site.
People who write malware also get their programs onto computers by attaching them to real programs that people want. This is most common with pirated programs. This is because the downloader was doing something illegal and cannot complain to the authorities without getting in trouble themselves.[15] However, some non-piracy websites also put malware (or other unwanted programs that are almost as bad as malware) in a download with real, legal software in a process known as bundling. Computer security experts complain about websites that bundle real software with malware. Their complaints do not always stop the websites from bundling.[16]
Kinds of Malware
There are many different kinds of malware. Each acts a different way.
- Viruses are a kind of malware that need a user-run program to work.[17] They cannot copy themselves or move from one computer to another without a program to host it. Viruses are very common in pirated programs.[18] They can harm computers in many different ways, like deleting files and stealing passwords.[19]
- Worms are a lot like viruses and can cause the same kinds of damage. However, they’re able to move through the internet and copy themselves onto computers without help from a host program. This makes them more dangerous than a virus.[20] Worms are usually found in emails and drive-by downloads.[21]
- Trojan horses are like a much more dangerous version of a virus. They need a user to agree to run a program to work and cannot copy themselves from one computer to another. However, trojan horses can make the same problems a normal virus can make. They can also allow the malware writer to control the victim’s computer, install more malware, steal bank data, and more.[22] For example, ransomware is a type of trojan horse that stops a victim from using their files until they pay the person who wrote the malware.[23] Experts think that trojan horses are the most common type of malware in existence.[24]
- Adware is a type of malware that earns the program authors money with advertising. These programs show users ads and force them to use websites that make money for the malware writers. Adware will also find personal information about the victim (such as their age, race, and job). This is so the malware authors can sell the information to other people.[25] A user can usually uninstall adware easier than most malware. However, this is still difficult to do without a specially-designed program.[26]
- Spyware is a more dangerous kind of adware that steals more information from a user. Spyware can steal someone’s Internet traffic, account passwords, and anything they have typed into their computers. Spyware is also much harder to uninstall than adware is.[27]
Why Computers get Malware
There are a few reasons why computers get programs a user didn’t mean to install. One common reason is because of regular programs that have software bugs. Malware can use bugs, such as a buffer overflow, to make a program do something it was not designed to do.[28] Malware can also get onto a computer if it tricks a user into putting it there themselves. This can happen when a user plugs in a USB flash drive that has a virus on it already.[29] Malware also commonly uses social engineering to get users to run it, like pretending to be an important email attachment for work. Some malware even pretends to be an anti-malware program to get people to run it.[30]
How Malware is Stopped
Since malware is such a big problem, many companies make programs to try to stop it. These anti-malware programs have a lot of different ways to find malware. One is static analysis, which looks at the source code of a program before it is run. Then, if the program is similar to malware the static analysis program has seen before, the anti-malware program will stop the code from running. Another way of finding malware is dynamic analysis. Dynamic analysis runs only part of a program it is checking. If this part of the program tries to do anything that could be bad or harmful, the anti-malware program will not let the program run.[31]
Malware can also be stopped without a program. This can be done by not letting a computer connect to the Internet or other computers, called creating an air gap.[32] However, these computers can still get malware if someone puts it there another way. One example is when someone plugs in a USB drive that was already plugged into a computer with a virus.[33]
HTTP cookie
An HTTP cookie (usually just called a cookie) is a simple computer file made of text. The information stored in cookies can be used to personalise the experience when using a website. A website can use cookies to find out if someone has visited a website before and record information (data) about what they did.
When someone is using a computer to browse a website, a personalised cookie file can be sent from the website’s server to the person’s computer. The cookie is stored in the web browser on the person’s computer. At some time in the future, the person may browse that website again. The website can send a message to the person’s browser, asking if a cookie from the website is already stored in the browser. If a cookie is found, then the data that was stored in the cookie before can be used by the website to tell the website about the person’s previous activity. Some examples where cookies are used include shopping carts, automatic login and remembering which advertisements have already been shown.
Cookies have been a problem for Internet privacy. This is because they can be used to track browsing behavior. Because of this, laws have been made in some countries to protect people’s privacy. There are many other options than cookies, but each option has its own problems.
Cookies have often been mistaken for computer programs. But cookies cannot do much on their own. They are simply a piece of data. They are often called spyware or viruses, but they are not either of these.
Most web browsers allow users to choose whether to accept cookies. If the user does not allow cookies, some websites will become unusable. For example, shopping baskets which use cookies do not work if the user does not allow cookies.
Protocols
Hypertext Transfer Protocol
Hypertext Transfer Protocol (often abbreviated to HTTP) is a communications protocol. It is used to send and receive webpages and files on the internet. It was developed by Tim Berners-Lee and is now coordinated by the W3C. HTTP version 1.1 is the most common used version today. It is defined in RFC 2616.
HTTP works by using a user agent to connect to a server. The user agent could be a web browser or spider. The server must be located using a URL or URI. This always contains http:// at the start. It normally connects to port 80 on a computer.
A more secure version of HTTP is called HTTPS. This contains https:// at the beginning of the URL. It encrypts all the information that is sent and received. This can stop malicious users such as hackers from stealing the information. HTTPS is often used on payment websites.
Request Message
The request message contains the following:
- Request line, such as GET /images/logo.gif HTTP/1.1, which requests the file logo.gif from the /images directory
- Headers, such as Accept-Language: en
- An empty line
- An optional message body
The request line and headers must all end with two characters: a carriage return followed by a line feed, often written <CR><LF>. The empty line must consist of only <CR><LF> and no other whitespace. In the HTTP/1.1 protocol, all headers except Host are optional.
A request line containing only the path name is accepted by servers to maintain compatibility with HTTP clients before the HTTP/1.0 standard. Even this site has a HTTP at its beginning.
Wired Equivalent Privacy
Wired Equivalent Privacy (also known as WEP) is a standard to use encryption in Wireless LANs. It was introduced in 1999.
In 2001, mathematicians showed that WEP is not very strong. A WEP connection could be decoded, with software that can be easily found, within minutes.[34] Because of this finding, IEEE created a new 802.11i group to fix the problems. By 2003, the Wi-Fi Alliance announced that Wi-Fi Protected Access (WPA) would replace WEP, which was a subset of then upcoming 802.11i amendment. Finally in 2004, they made it official and said that it would go ahead. It was part of the full 802.11i standard (also known as WPA2), the IEEE declared that both WEP-40 and WEP-104 are not recommended because they are not secure enough.[35]
Even though it only offers low security, WEP is still widely in use.[36] WEP is often the first security choice presented to users by router configuration tools even. Today, WEP provides a level of security that deters only accidental use. As a result, people can invade and enter the network.[37]
People sometimes call it Wireless Encryption Protocol, which is wrong.
Wi-Fi Protected Access
Wi-Fi Protected Access (also known as WPA and WPA2) is the name for a number of standards to use encryption on a Wireless LAN. The standards were created because researchers had found several weaknesses in Wired Equivalent Privacy. Wired Equivalent Privacy, or WEP was the standard that came before it. The protocol WPA2 implements most of the standard IEEE 802.11i.
Products that have the label WPA were designed to work with most cards, even those that came out before there was WPA. This is not true for access points though.
Products with the WPA2 implement all of the standard. This is more secure, but it may not work with some older cards.
Protection
Encryption
Encryption is a method which allows information (for example, a secret message) to be hidden so that it cannot be read without special knowledge (such as a password). Once this is done, using a secret code or cypher, the information is encrypted. Decryption is a way to change an encrypted piece of information back into unencrypted form. This is called the decrypted form. The study of encryption is called cryptography.
Examples
A simple kind of encryption for words is ROT13. In ROT13, letters of the alphabet are changed with each other using a simple pattern. For example, A changes to N, B changes to O, C changes to P, and so on. Each letter is “rotated” by 13 spaces. Using the ROT13 cipher, the words Simple English Wikipedia becomes Fvzcyr Ratyvfu Jvxvcrqvn. The ROT13 cipher is very easy to decrypt. Because there are 26 letters in the English alphabet, if a letter is rotated two times by 13 letters each time, the original letter will be obtained. So applying the ROT13 cipher a second time brings back the original text. When he communicated with his army, Julius Caesar sometimes used what is known as Caesar cipher today. This cipher works by shifting the position of letters: each letter is rotated by 3 positions.
Most kinds of encryption are more complex. Some are made only for text. Others are made for binary computer files like pictures and music. Today, the asymmetric encryption system used the most is RSA. Any computer file can be encrypted with RSA. AES is a common symmetric algorithm.
One-Time Pad
Most types of encryption can theoretically be cracked: an enemy might be able to decrypt a message without knowing the password, if he has clever mathematicians, powerful computers and lots of time. The one-time pad is special because, if it is used correctly, it is impossible to crack. There are three rules that must be followed:
- The secret key (password) must be longer than the secret message: if the message has 20 letters then the key must also have at least 20 letters.
- The secret key must be a random list of letters (e.g. KQBWLDA…)
- The secret key must only be used once. To send more than one message, a different key must be used for each one.
If these three rules are obeyed, then it is impossible to read the secret message without knowing the secret key. For this reason, during the Cold War, embassies and large military units often used one-time pads to communicate secretly with their governments. They had little books (“pads”) filled with random letters or random numbers. Each page from the pad could only be used once: this is why it is called a “one-time pad”.
Encryption on the Internet
Encryption is often used on the Internet, as many web sites use it to protect private information. On the Internet, several encryption protocols are used, such as Secure Sockets Layer (SSL), IPsec, andSSH. They use the RSA encryption system and others. The protocol for protected web browsing is called HTTPS. Mostly URL encryption contain MD5 Algorithm. Various algorithms are used in the internet market depending upon the need.
Antivirus Software
Antivirus software, if properly installed on a computer system, can prevent access to computer systems by unwanted computer programs. Viruses, worms or Trojan Horses can be used by criminals or mischievous people (called Crackers). They can be used to steal information or damage computer systems. If no antivirus software is installed, hackers may be able to access the information in the computer.
Most tests and experts claim that antivirus software is unable to prevent all attacks.[38] There are many different types of antivirus software. Many Antivirus programs can be downloaded for free. These versions usually have some features missing. The missing features are only available to those who buy the “full” version.
Antivirus software uses many ways to protect the computer. They often search for signs of viruses in every website that is visited. Most also do a regular scan of all the data and files on the computer’s hard disk.
Installing more than one antivirus is not a good idea. The 2 different antivirus software can interfere with each other.
Problems with Antivirus Software
Antivirus software can not always detect all viruses on a computer.
Sometimes antivirus software sees viruses in files that do not really have viruses. This is called a false positive.[39] The antivirus software will sometimes remove files from the computer that should not be removed. This may cause other programs to not work properly.
Firewall (Networking)
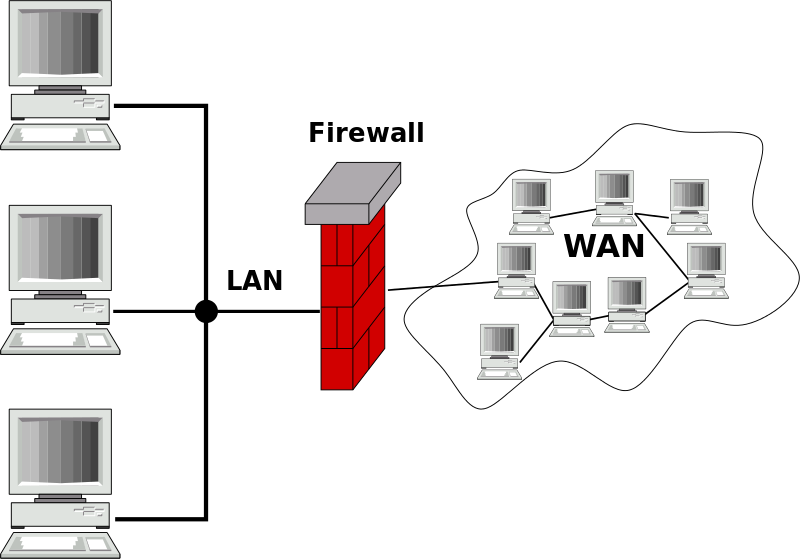
Originally, a firewall was a wall that was built to stop (or slow down) the spread of a fire. In terms of computer security, a firewall is a piece of software. This software monitors the network traffic. A firewall has a set of rules which are applied to each packet. The rules decide if a packet can pass, or whether it is discarded. Usually a firewall is placed between a network that is trusted, and one that is less trusted. When a large network needs to be protected, the firewall software often runs on a dedicated hardware, which does nothing else.
A firewall protects one part of the network against unauthorized access.
Different Kinds of Firewalls
- Packet filtering. Data travels on the internet in small pieces; these are called packets. Each packet has certain metadata attached, like where it is coming from, and where it should be sent to. The easiest thing to do is to look at the metadata. Based on rules, certain packets are then dropped or rejected. All firewalls can do this.it is known as network layer
- Stateful packet inspection. In addition to the simple packet filtering (above) this kind of firewall also keeps track of connections. A packet can be the start of a new connection, or it can be part of an existing connection. If it is neither of the two, it is probably useless and can be dropped.
- Application-layer firewalls. Application-layer firewalls do not just look at the metadata; they also look at the actual data transported. They know how certain protocols work, for example FTP or HTTP. They can then look if the data that is in the packet is valid (for that protocol). If it is not, it can be dropped.
Other Things Firewalls Are Used For
Firewalls can provide a secure connection between two networks. This is called tunnelling. The data may be encrypted. It is unencrypted at the other end. Since the firewalls are doing this, the rest of the network is unaware of it. An alternative is to provide a secure access (to the corporate network).
Network Address Translation
Very often, firewalls can translate IP addresses. That way, many computers can share a few public IP addresses. The firewall translates between the public and the private IP addresses.
Types of Firewalls
In general, there are two types of firewalls:
- Software-based firewalls: these are often run as additional programs on computers that are used for other things. They are often known as personal firewalls which can be updates on personal computers.
- Hardware-based firewalls: Hardware based firewalls run on a dedicated computer (or appliance). Often, these offer a better performance than software firewalls, but they are also more expensive.
What Firewalls Cannot Protect Against
Firewalls can protect against some problems (viruses and attacks) that come from the internet. They cannot protect against viruses, that come from infected media (like an infected office document on an USB flash drive).
Backup

A backup is a copy of some data. This copy can be used when the original data is changed, or lost. Losing data is common: A 2008 survey found that two thirds of respondents had lost files on their home PC.[40] Another purpose of backing up data is to have a copy that represents an earlier state of the data, before it was changed. Organisations may have rules which state how long data should be kept, and what kinds of data these rules apply to. In many countries there are rules that specify that certain kinds of data need to be kept for a given time. An example of this is the data used for accounting.
Backups are a simple form of disaster recovery. Even though they are commonly seen as disaster recovery, they should be part of a disaster recovery plan. A disaster recovery plan is a documented set of procedures and tasks to perform to protect the consistency and integrity of a corporate IT system.
Different Backup Media
There are different types of backup systems that use different kinds of media. Common backup media includes:
- Different kinds of tapes, for example Digital Audio Tape, or LTO
- Hard disks
- Optical disks like CDs and DVDs
- Magneto-Optical Discs
- Emails

Some of the backup media are portable, and can easily be stored in a safe location. The problem with storing tapes in a bank safe, for example is that they are only available during the opening hours of the bank.
Another issue has commonly been the speed of the backup. Media such as digital tapes can store a lot of data, but accessing them is realtively slow. Tapes can only be read or written in sequence, while media such as hard disks or optical drives are basically random access. When data is backed up, its encoding is often changed. This makes it possible to use codes such as Cyclic redundancy checks, which can detect, and sometimes repair an error.
Reasons for Doing a Backup
Backups are usually done for one of the following reasons:
- Prevent data loss if there is a disaster (like a fire or hardware failure, or an intentional or unintentional deletion)
- Computer viruses or other programs make data unusable
- There is a logical error in the data
- Sudden computer shutdown which can be caused by power shortage.
Different Types of Backup
- A full backup copies all of the data. This means that if the main copy of the data is lost, we can bring it all back simply by copying the data back from the backup.
- A differential backup only copies the data that has changed since the last full backup. The reason we do this is that sometimes only a small amount of data has changed since the last full backup; this means we can do a differential backup much more quickly. If someone loses their data, and needs to get it back from a differential backup, they need to use the last full backup, to bring back all of their data. They then need to use the last differential backup to bring back everything that was changed between the full backup and the differential backup.
- An incremental backup only copies the data that has changed since the last incremental backup. This makes each backup quicker, because we are only copying what has changed since the last backup. To bring the data back, if the main copy of the data is lost, we need the last full backup, as well as all of the incremental backups that have been done since then. This means that bringing data back from an incremental backup is slower and more risky than differential or full backups.
How Long to Keep a Backup
The Grandfather-father-son system means that we keep different types of backup for different amounts of time. For example, we might do a backup every day, and keep a week’s worth of backups. We might then keep one backup for each week for a month, and one backup from each month for a year. This means that we have a backup of our data from a year ago, so that if we realise we need some data from a long time ago, we have that data available. We also have several copies of our recent data, in case one of them doesn’t work.
- Leyden, John. "The 30-year-old prank that became the first computer virus". The Register. Retrieved 1 November 2014. ↵
- Dalakov, Georgi. "First computer virus of Bob Thomas". Retrieved 1 November 2014. ↵
- Lee, Timothy. "How a grad student trying to build the first botnet brought the Internet to its knees". Washington Post Company. Retrieved 1 November 2014. ↵
- Messmer, Ellen. "Tech Talk: Where'd it Come From, Anyway?". IDG Consumer & SMB. Retrieved 11 November 2014. ↵
- File, Thom. "Computer and Internet Use in the United States". U.S. Census Bureau. Retrieved 11 November 2014. ↵
- "The Evolution of Malware and the Threat Landscape – a 10-Year review". Microsoft Incorporated. Retrieved 11 November 2014. ↵
- "Annual Report PandaLabs 2013 Summary". Panda Security. Retrieved 15 November 2014. ↵
- Cannell, Joshua. "Cryptolocker Ransomware: What You Need To Know". Malwarebytes Corporation. Retrieved 1 November 2014. ↵
- "Virus: DOS/CIH". F-Secure Corporation. Retrieved 1 November 2014. ↵
- Grebennikov, Nikolay. "Keyloggers: How they work and how to detect them (Part 1)". Kaspersky Labs. Retrieved 11 November 2014. ↵
- Kushner, David. "The Real Story of Stuxnet". IEEE. Retrieved 1 November 2014. ↵
- Greenberg, Andy. "Evidence Mounts That Chinese Government Hackers Spread Android Malware". Forbes Media. Retrieved 1 November 2014. ↵
- "How Malware Attacks And Spreads In Your Computer". Combofix. Retrieved 2 November 2014. ↵
- Siciliano, Robert. "What is a “Drive-By” Download?". McAfee Incorporated. Retrieved 2 November 2014. ↵
- "How Malware Attacks And Spreads In Your Computer." ↵
- Lemos, Robert. "Security pros slam Cnet Download.com's bundling". InfoWorld Incorporated. Retrieved 2 November 2014. ↵
- "What Is the Difference: Viruses, Worms, Trojans, and Bots?". Cisco Systems, Incorporated. Retrieved 3 November 2014. ↵
- "How Malware Attacks And Spreads In Your Computer." ↵
- "What Is the Difference: Viruses, Worms, Trojans, and Bots?" ↵
- "What Is the Difference: Viruses, Worms, Trojans, and Bots?" ↵
- Siciliano, Robert. ↵
- "What is a Trojan Virus?". Kaspersky Lab. Retrieved 3 November 2014. ↵
- Cannell, Joshua. ↵
- "Annual Report PandaLabs 2013 Summary." ↵
- "What is Adware?". Kaspersky Labs. Retrieved 3 November 2014. ↵
- "Adware". Bleeping Computer LLC. Retrieved 3 November 2014. ↵
- Beal, Vangie. "The Difference Between Adware & Spyware". Quinstreet Incorporated. Retrieved 3 November 2014. ↵
- Schwarz, Thomas. "Buffer Overflow Attack". COEN, SCU. Retrieved 6 November 2014. ↵
- Mills, Elinor. "USB devices spreading viruses". CBS Interactive Incorporated. Retrieved 6 November 2014. ↵
- "Social Engineering". Kaspersky Labs. Retrieved 6 November 2014. ↵
- "Heuristic analysis in Kaspersky Internet Security 2012". Kaspersky Lab. Retrieved 4 November 2014. ↵
- "Air Gap". Janalta Interactive Incorporated. Retrieved 6 November 2014. ↵
- Mills, Elinor. ↵
- Nikita Borisov, Ian Goldberg, David Wagner. "Intercepting Mobile Communications: The Insecurity of 802.11". Retrieved on 12 September 2006. ↵
- "What is a WEP key?". lirent.net. Retrieved on 11 March 2008. ↵
- "Wireless Adoption Leaps Ahead, Advanced Encryption Gains Ground in the Post-WEP Era". RSA.com. Retrieved on 11 March 2008. ↵
- Andrea Bittau, Mark Handley, Joshua Lackey. "The Final Nail in WEP's Coffin". Retrieved on 16 March 2008. ↵
- Shaw, Gordon. "AV-Test release latest results."Virus Bulletin. Retrieved 8 March 2009. ↵
- http://www.offlinetalk.com/index.php/topic,106.msg169.html ↵
- Global Backup Survey. Retrieved on 15 February 2009 ↵
Contributors and Attribution
- Computer security. Provided by: Wikipedia. Located at: https://simple.Wikipedia.org/wiki/Computer%2520security?oldid=5031991. License: CC BY-SA: Attribution-ShareAlike
- Malware. Provided by: Wikipedia. Located at: https://simple.Wikipedia.org/wiki/Malware?oldid=4948052. License: CC BY-SA: Attribution-ShareAlike
- HTTP Cookie. Provided by: Wikipedia. Located at: https://simple.Wikipedia.org/wiki/HTTP%2520cookie?oldid=5031056. License: CC BY-SA: Attribution-ShareAlike
- Hypertext Transfer Protocol. Provided by: Wikipedia. Located at: https://simple.Wikipedia.org/wiki/Hypertext%2520Transfer%2520Protocol?oldid=4118562. License: CC BY-SA: Attribution-ShareAlike
- Wired Equivalent Privacy. Provided by: Wikipedia. Located at: https://simple.Wikipedia.org/wiki/Wired%2520Equivalent%2520Privacy?oldid=4598792. License: CC BY-SA: Attribution-ShareAlike
- Wi-Fi Protected Access. Provided by: Wikipedia. Located at: https://simple.Wikipedia.org/wiki/Wi-Fi%2520Protected%2520Access?oldid=4559244. License: CC BY-SA: Attribution-ShareAlike
- Encryption. Provided by: Wikipedia. Located at: https://simple.Wikipedia.org/wiki/Encryption?oldid=4964670. License: CC BY-SA: Attribution-ShareAlike
- Antivirus Software. Provided by: Wikipedia. Located at: https://simple.Wikipedia.org/wiki/Antivirus%2520software?oldid=4923125. License: CC BY-SA: Attribution-ShareAlike
- Firewall (networking). Provided by: Wikipedia. Located at: https://simple.Wikipedia.org/wiki/Firewall%2520(networking)?oldid=5035455. License: CC BY-SA: Attribution-ShareAlike
- Backup. Provided by: Wikipedia. Located at: https://simple.Wikipedia.org/wiki/Backup?oldid=4918638. License: CC BY-SA: Attribution-ShareAlike


